14/03/2023
8 ways to protect employees who are using public WiFi
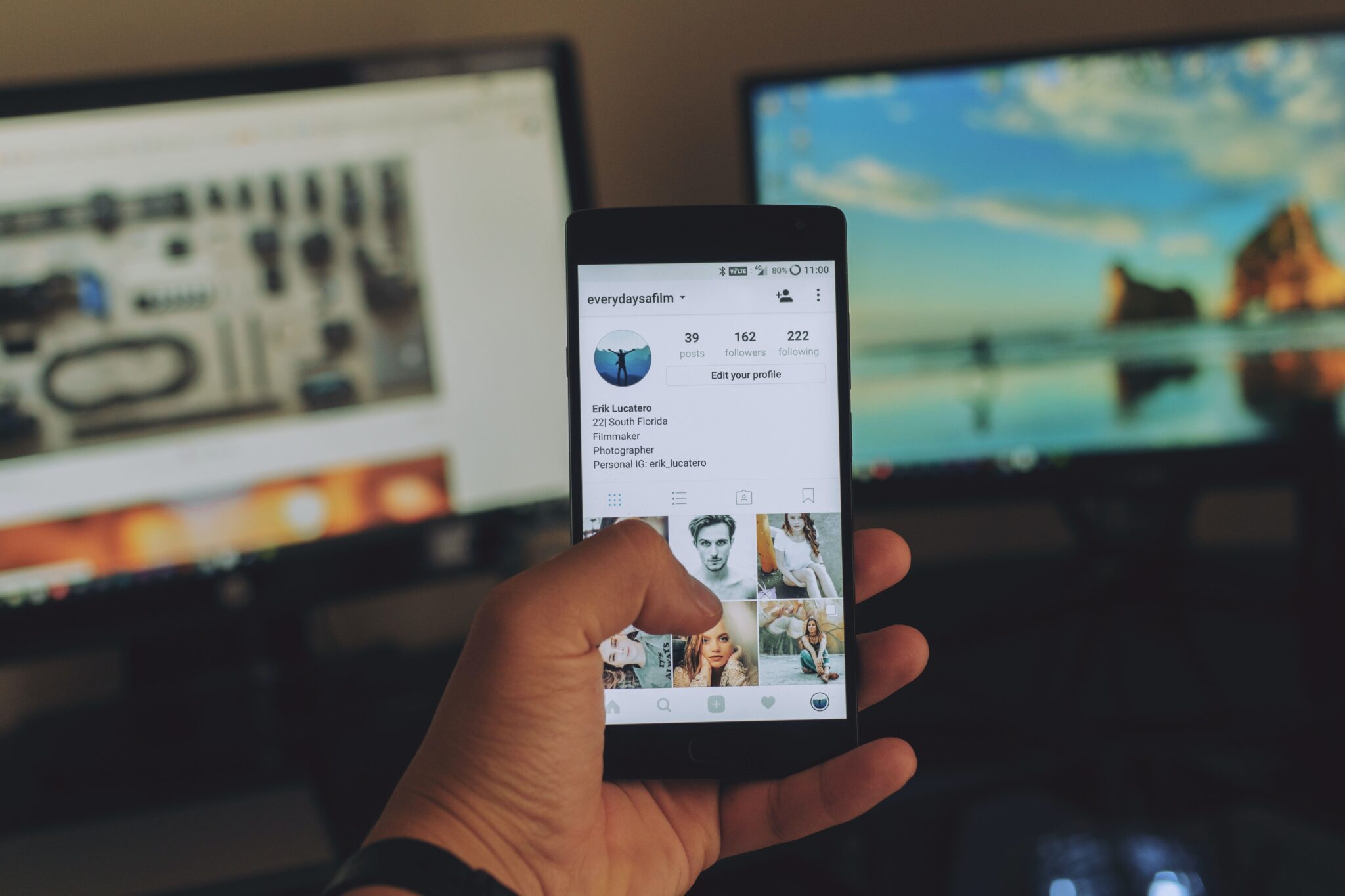
Maintaining the security of employee endpoints is an important consideration for any organisation, especially when employees are using public WiFi…
Tech Driven. People Powered.
Insights, analysis, and thought leadership from the front lines of cybersecurity. Our blog covers emerging threats, best practices, and expert perspectives to help you stay secure in a constantly evolving digital world.


14/03/2023
Maintaining the security of employee endpoints is an important consideration for any organisation, especially when employees are using public WiFi…

28/02/2023
Employee burnout is a serious issue that can have a significant impact on a company’s cyber security. Burnout is a…

27/02/2023
SEP2 continues to grow and strengthen our relationship with Check Point. SEP2 have been a partner of Check Point since…

03/02/2023
SEP2’s 7th Birthday This week at SEP2, we are proud to be celebrating our 7th Birthday. Much has changed over…
31/01/2023
How cyber criminals exploit human nature, and what you can do to stop them. Social engineering is a tactic used…

14/12/2022
This year has been filled with positives for SEP2 as we have continued to grow and evolve as an organisation….

25/08/2022
From cereal box whistles to billion-dollar breaches: five hacks that made history. Today the word “Hacker” is synonymous with individuals…

11/07/2022
Why cybercriminals are targeting smaller companies—and how to fight back You often will see stories in the news about large…

31/05/2022
A new zero-day remote code execution bug has been found in Microsoft Office. This was first picked up by security…
14/04/2022
Technology is at the centre of almost everything in modern-day life, and the world of sport is no exception. Where…
10/03/2022
Reflecting on the impact, challenges, and future of data protection in a post-GDPR world It’s been four years since GDPR…

08/03/2022
Unpacking the statistics, the stereotypes, and the steps toward a more inclusive future The Tech Sector is a rapidly growing…
.